An intensive Distributed Denial of Service attack is currently undergoing on my blog, with HTTP request rates hitting thousands per minute. It all started few days ago when I received a message from my hosting service provider stating that my blog’s shared hosting has massive CPU/Bandwidth usage. The folks offered a solution for me that was “upgrade to a higher plan so you can meet the DDoS traffic”.. I was speechless and had to take things under my control.
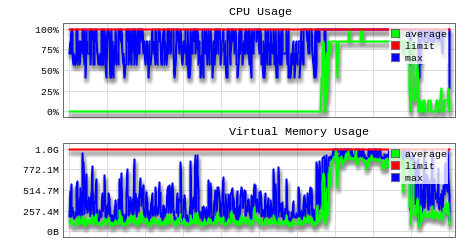
Looking at the stats, the attack start moment is also obvious:
During the peak of the attack my blog was mostly down.
Victims to DDoS often ask themselves the same questions, “why” and “why me”. Generally for this type of attacks the “why” boils down to these cases
- blackmailing for money
- blocking competition
- attempting censorship
- mischief
I can’t imagine my humble personal blog falls into any of the first three categories and believe it is someone just being playful.
The attack is on-going (as I write these lines) from numerous IP addresses all over the world, but fortunately for me it is being executed in a not very smart way, so I was able to pick up a trend and catch these via a smart updating .htaccess “deny from” rule. I can’t give out much details on the exact measures as the attacker could be reading this and adjust.
The result from this blocking is obvious from the above graphs and my blog is up again.
Yep, ddos is a pain. You might take a look at cloudflare’s free service. There might be other free ddos services as well.
Indeed it is a PIA, but also awakening reminder to harden up security. Thanks for the pointer
I wondered already why I got those time outs while trying to visit your website 😉
I’m using WordFence (free version) that is able to automatically throttle & block/ban IP’s that issue to many HTTP requests to a wordpress site.
No idea however if that mechanism also works for this kind of attack though!
As you are now hosting @ DigitalOcean, I thought that they let you add rules in the iptables firewall (rate limiting) which could help also for automatic blocking or over enthousiastic users…
I see now that you are already using WordFence…
Wordfence alone wasn’t helping much. The DDoS (still undergoing btw) is carried out from a constantly changing poll of zombie computers. (100+ as of today) What wordfence does is to redirect those to a wordpress generated HTTP 503 page that is >2K, resulting in a still quite stressed out Apache server. Imagine handling few thousands of these per second on a VPS with 512MB RAM. What I am actually doing is to have wordfence identify the naughty IPs and then update my .htaccess with a deny rule (wordfence sends email to a monitoring account that kicks in a .htaccess update script). What would probably work best though (and as you suggest) is a fail2ban rule that blocks these IPs using a firewall rule. That would mean the requests don’t even reach Apache and the VPS would handle a really massive DDoS easily.
Pingback: Free signed SSL certificate for my blog | Martin's corner on the web
Pingback: My own cloud version control tool | Martin's corner on the web